Cybersecurity
Staying Secure Online: Your Defense Against Cyber Threats
It's time to fortify your online defenses! In this final part of our series, we'll share practical tips to keep your financial information safe.
In this part, let's address three cognitive biases that can make us vulnerable:
• Authority Bias: Pertains to individuals' accuracy based on the opinion of authoritative figures, such as a manager, boss, or CEO.
• Optimism Bias: This bias causes users to overestimate the chance of positive events, making them susceptible to unbelievable job offers or pay hikes in phishing emails.
• Curiosity Effect: Also referred to as the Pandora effect, when a user faces uncertainty and wants to resolve it, they will act, even though they don't know the outcome.
Cybercriminals use this to entice users into clicking on intriguing but malicious links.
Remember, reporting suspicious messages and verifying the authenticity of communications are vital steps to staying secure. Explore the resources and tools we offer to protect your online security. Together, we can outsmart cyber threats and safeguard your financial well-being!

Hacker's Playbook: How Cybercriminals Exploit Your Brain
Did you know that hackers often rely on our cognitive biases to manipulate us? In this part, we'll delve into the world of cyber threats.
In this part, let's focus on three cognitive biases hackers exploit:
• Halo Effect: This is the tendency for individuals to trust entities they have a positive impression of. Cybercriminals pretend to be the trusted entity.
• Loss Aversion: This refers to an individual's avoidance of losses, which cybercriminals might exploit to create a sense of urgency.
• Ostrich Effect: This is a fear tactic that convinces users they've done something wrong and must click a link to avoid reprimand, sticking their heads in the sand, so to speak.
Don't fall prey to their tricks!
Stay vigilant and educated to protect your online security. Understanding these biases is the key to staying one step ahead of cybercriminals.
Part 1: Understanding Cognitive Biases
Uncover the Secrets of Your Decision-Making:
Ever wondered why you make certain decisions without even realizing it????
It's all thanks to cognitive biases, which are the shortcuts our brains use to process information. In this series, we'll explore how these fascinating mental quirks impact our daily lives.
In this part, let's look into three cognitive biases:
1. Hyperbolic Discounting: This bias makes us prefer small, immediate rewards over larger, delayed ones, often leading to impulsive decisions.
2. Habit: This bias takes advantage of users who follow recurring habits, building social engineering attacks around regular emails and other communications.
3. Recency Effect: This bias triggers individuals to remember the most recent events that have taken place, which cybercriminals may use to lure targets with events like the COVID-19 pandemic and global occurrences.
Knowledge is power, especially when it comes to safeguarding your financial security! Stay tuned for part 2 so we can uncover more ways that cognitive biases can affect our lives.

.png)
.png)

Embracing the Power of AI: Dos and Don'ts for a Safer Digital World
In the heart of our community, where businesses thrive, and families connect, the digital landscape has become an integral part of our lives. It's where we shop, learn, work, and share our stories. This Cybersecurity Awareness Month, we come together to explore the promises and challenges of Artificial Intelligence (AI) – a technology that holds the potential to revolutionize our lives but also brings new security concerns.
Dos
• Understand the Technology: Before Using AI tools, take the time to understand how to they work, their capabilities, and limits.
• Choose Reputable AI Tools: To make the right choice, research the developer, check for reviews, verify security measures, evaluate ethical considerations, inquire about support, and stay informed about AI developments.
• Ensure Data Privacy: Although AI is a very new and exciting world of the unknown you must be sure that the data, you’re inputting into these systems isn’t confidential or sensitive.
• Experiment and Learn: AI can perform a wide range of tasks. You simply just need to experiment with it to find what works best for your work and personal needs.
Don’ts
• Over-Reliance: While AI can provide helpful suggestions for many situations, you mustn’t rely on AI-generated outcomes without your own critical thinking and judgment.
• Unverified Information: Always verify the accuracy of AI-generated information, especially if it’s critical to your job and decisions about your job.
• Unintended Consequences: Be cautious of biases in AI models, they can sometimes unintentionally produce biased results, which can sometimes have negative implications.
Remember, cybersecurity is a collective effort, and we, as a community, have the strength to shape the future of the digital world. By staying informed, sharing knowledge, and implementing these do's and don'ts, we can build a resilient, secure, and thriving digital ecosystem for ourselves, our businesses, and our loved ones.
5 Simple Web Browsing Tips
Hey there, cyber-savvy community!
In today's digital world, staying safe while surfing the web is crucial. We've got your back with 5 simple web browsing tips that anyone can follow. Whether you're a tech pro or just getting started, these tips will help protect your online presence and information. Let's dive in!






Part 3: Ransomware 101 - Ransomware Realities - Consequences, Resolution, and Recovery
As we enter the last section of our ransomware series, we'll explore the aftermath of a ransomware attack and the difficult path to recovery. We'll examine the issues that can arise and provide you with the steps to mend the situation, giving you a clear picture of what awaits on the other side. Understanding this process is crucial for ensuring the security of your digital life.
Consequences:
- Financial Fallout: Ransomware can result in significant expenses, including potential legal fees and overall financial damage for both businesses and individuals. It's similar to getting an unexpectedly large bill that you must settle to regain control of your digital life.
- Data Disarray: The loss of vital data and potential exposure of personal information, can cause long lasting damage to a businesses' reputation and diminish customer trust. For individuals it's like loosing precious items, and not know if you will ever get them back.
- Emotional Stress: Ransomware isn't just about money and data; it can mess with your emotions too. Imagine the anxiety and frustration of suddenly losing access to your important files.
Resolution:
Assess the Damage: You must first identify the what files and systems have been affected, and determine the type of ransomware that your dealing with.
Data Recovery and the tools used to get it back:
- Backup Restoration: If you have up-to-date backups that were not compromised in the attack, this is one way to restore your data.
- Decryption Tools: Some variants of ransomware have decryption tools available, check with a cybersecurity expert or local law enforcement for assistance in unlocking your encrypted files.
- Professional Assistance: It is best practice to seek out a cybersecurity professional to evaluate your unique situation and offer the best data recovery strategies.
Recovery:
Rebuilding Security: After regaining your data, you must focus on rebuilding your digital defense. Consider the following steps:
- Security Updates: Ensure that all software and systems are up to date and to patch any vulnerabilities that ransomware may exploit.
- Security Software: Invest in reputable antivirus and anti-ransomware software.
- Individual and Employee Training: Education is key to staying on top of the best practices to reduce the likely chance of becoming victim to phishing or similar attacks.
- Network Security: Review and enhance network security measures to prevent unauthorized access.
As we finish our series on ransomware, we've covered a lot about how to stay safe from these online threats. Remember, knowing what to do and being prepared are your best allies. By learning and practicing good cybersecurity, you can protect yourself from ransomware and keep your digital life secure.
Stay safe and be smart online!

Part 2: Ransomware 101 - Defending Against Ransomware: Knowing Your Enemy & What to Do in the Event of an Attack
As we enter into the world of ransomware defense, it's crucial to understand that knowledge is your strongest defense. In this section, we will equip you with the tools to protect yourself against ransomware, but we'll also prepare you for the unlikely event of an attack. By understanding your enemy and knowing what to do if the worst happens, you'll be better prepared to safeguard your digital life.
Ransomware Defense Strategies:
Update Everything: Think of software updates like repairing a leaky roof. Just as a neglected leak can lead to significant damage over time, outdated software can leave your digital defenses vulnerable to cyberattacks.
Strong Passwords: Consider strong passwords as the locks on your doors. You wouldn't leave your home unlocked, so don't leave your digital accounts unprotected with weak passwords.
Email Caution: Treat suspicious emails like unsolicited phone calls. You wouldn't give personal information to an unknown caller, so avoid clicking on links or sharing sensitive data with unknown email senders.
Backup Regularly: Regular backups are like insurance for your data. Just as you have insurance to cover unexpected events in the physical world, backups protect your digital information in case of a ransomware attack.
Security Software: Think of antivirus software as a security guard for your computer. You wouldn't leave your home or office unguarded, so invest in reliable security tools to watch over your digital space.
Safe Downloads: Downloading from trusted sources is like buying products from reputable stores. You wouldn't purchase items from an unverified street vendor, so be cautious when downloading software from unknown websites.
Stay Informed: Staying updated on cybersecurity threats is similar to being aware of current events in your neighborhood. Just as you keep an eye out for local news, stay informed about the latest cyber threats to protect yourself online.
Preparing for the unthinkable - In Case of an Attack:
While we all aim to dodge ransomware, reality can hit hard. If you suspect ransomware's got you in its grip, brace yourself with these information saving steps:
• Ransomware Attack? Don't Panic, Act Smart!
• Isolate the Device: Unplug to stop the spread!
• Don't Pay Ransom: Resist! No guarantees, and it funds cybercriminals.
• Report the Incident: Notify authorities ASAP. It's essential!
• Quarantine and Document: Keep evidence like a detective.
• Seek Professional Help: Call in cybersecurity experts.
• Restore from Backups: Your digital safety net!
• Enhance Security: Fortify defenses for the future.
• Stay Informed: Knowledge = Power! Be vigilant.
So, remember that knowledge is your armor, and preparation is your shield. By understanding the strategies to protect yourself and being ready to respond in the unlikely event of an attack, you're building a strong fortress around your digital life. Stay alert and informed and be looking for part 3 of the series where well explore the consequences and resolution strategies following a ransomware attack.
Stay safe online!

Part 1: Ransomware 101 - Understanding the Threat
In today's interconnected digital world, understanding the threat of ransomware is essential for safeguarding your financial well-being. In this section, we will delve into the world of ransomware, providing you with the knowledge you need to protect yourself.
What is Ransomware? Ransomware is a type of malicious software (malware) that sneaks into your computer or network, locks up your files, and then demands money (ransom) in exchange for the key to unlock them.
Ransomware Statistics:
To give you an idea of how serious the threat is, consider these facts:
• In 2023, there have been 1,900 reported ransomware attacks worldwide.
• Cybercriminals are now demanding an average of over $200,000 in ransom, making it a highly profitable criminal business.
• 41% of these ransomware attacks start with phishing emails.
So, how do ransomware attacks happen you might ask? They can occur in various ways and circumstances, but below are the most common ways that ransomware could enter your system.
1. Phishing/Spear Phishing Emails: Bad actors send deceptive emails with harmful links or attachments. If you unknowingly click on them, it can trigger the ransomware attack. Think of it as an email that looks innocent but hides a dangerous secret.
2. Malicious Downloads: Sometimes, downloading software or files from sketchy or untrusted websites can bring ransomware into your device. It's like getting a hidden virus while trying to download something you wanted.
3. Exploiting Vulnerabilities: When your computer's software is not up to date or has security holes, cybercriminals can sneak in through those gaps. It's like leaving your front door unlocked for burglars.
Now that you understand what ransomware is and how it can happen, please stay aware and be ready for part 2 of the series where we'll explore how to protect yourself from this digital threat and what to do if you become a victim.
Your financial safety is at stake, so stay tuned to learn how to defend against ransomware!
The Power of Strong Passwords
As part of our ongoing series for Cybersecurity Awareness Month, we want to talk about something that affects us all—the use of strong passwords
What is a Password?
Think of it as your digital key, your secret handshake with the online world. It's the code that lets you access your digital life, just like your PIN for your bank card.
Why are strong passwords crucial for our community? When we all use strong passwords, we're not just protecting ourselves; we're protecting our neighbors, our friends, and our local businesses. We all store personal and financial information online. Strong passwords are the lock and key to a large treasure chest that's keeping our data safe.
The Dos and Don’ts for Creating Strong Passwords
Dos:
• Complexity is Key: Combine uppercase and lowercase letters, numbers, and symbols to add complexity to your passwords. For example: "WYFexs123!@#".
• Be Unique: Create passwords that are unique and unrelated to common words or phrases. Avoid using easily guessable information like "password," "123456," or "qwerty."
• Variety is Strength: Develop different passwords for various accounts. Using the same password across multiple accounts increases your vulnerability.
• Passphrases are Powerful: Consider using passphrases, which are longer and easier to remember. Combine unrelated words, include numbers, and add special characters. For instance, "BlueSky$Pizza42%Forest!"
Don'ts:
• No Repetition: Avoid repeating characters or numbers in your passwords. Patterns like "aaaaa" or "232323" are easy to crack.
• Common Words are Risky: Stay away from common words, even with minor variations or character substitutions. Never use "password" or "p@ssw0rd."
• Avoid Sequential Characters: Refrain from using sequential characters like "12345" or predictable keyboard patterns like "asdfg" or "hjkl;."
• Personal Info is Off-Limits: Never include easily accessible personal information, such as your name, birthdate, or family members' names, in your passwords.
Longer is Stronger: Longer passwords are generally more secure. Aim for a minimum of 12 characters for added protection.
We understand that managing a unique, password for each of your accounts might seem like an inconvenience. However, the importance of this practice cannot be overstated. Think of it this way: it's your shield against a domino effect, where one compromised password can unlock your entire digital life. Having different passwords for different accounts builds layers of security; even if one account is breached, the rest remain safe. Plus, it's like having tailored protection for various aspects of your online world, from banking to email and social media. By avoiding predictability and keeping cybercriminals guessing.
So, the next time you set up a new password, envision it as a piece of the larger puzzle—a puzzle that keeps your digital life secure and outsmarts cybercriminals. By working together to create a safer online community, we can make cyberspace a place where we all thrive securely.
Stay vigilant, stay secure, and stay connected to protect what matters most.

Two-Factor (2FA) & Multi-Factor (MFA) Authentication
As part of our ongoing series for Cyber Security Awareness Month, we're back with another crucial tip to help safeguard your digital life.
Today, we wanted to take a moment to chat about something really important in the world of cybersecurity - Two-Factor (2FA) and Multi-Factor Authentication (MFA).
2FA and MFA are used to add an extra layer of security to your digital accounts and online transactions. Essentially, they ensure that it's not just your password protecting your account.
Let's start with the basics.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is an extra layer of security that requires users to provide two forms of identification to access their account or complete a transaction. This typically involves entering a password and then providing a unique code that is sent to the user's device, such as a phone or email, before gaining access. This adds an extra layer of protection against unauthorized access, as it is much more difficult for someone to gain access without both forms of identification.
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) takes it one step further and adds additional forms of identification such as biometric data (e.g. fingerprint or facial recognition), security tokens, or even physical keys. This provides an even higher level of security and is becoming increasingly popular in industries where sensitive information is involved, such as finance and healthcare.
Why should we use them? Well, apart from giving you an extra layer of security, it also provides peace of mind knowing that your sensitive information is well-protected. It's like having a guard dog, security cameras, and a high-tech alarm system all working together to protect your house.
But let's be real, using 2FA and MFA can sometimes feel like a hassle. Having to enter extra codes or use additional devices can be time-consuming and frustrating. However, the inconvenience is worth it for the added security it provides. Plus, many companies are now making it easier by offering options such as biometric authentication or mobile apps that generate unique codes.
So, next time you're setting up a new account or completing an online transaction, remember to enable 2FA and MFA if possible. It may seem like a small extra step, but it can make a big difference in keeping your personal information safe from cyber threats. Remember, in the digital world, security isn't just an option; it's a necessity.
Stay safe online, everyone!

October is Cyber Security Awareness Month!
As we increasingly live our lives online, it's crucial that we all understand the importance of protecting our digital presence. That's why this October, we're dedicating an entire month to raising awareness about cyber security!
Throughout this month, we will be sharing invaluable tips and best practices to help you stay safe in the cyber world. So, make sure you follow our page to receive regular updates and become a part of this significant campaign!
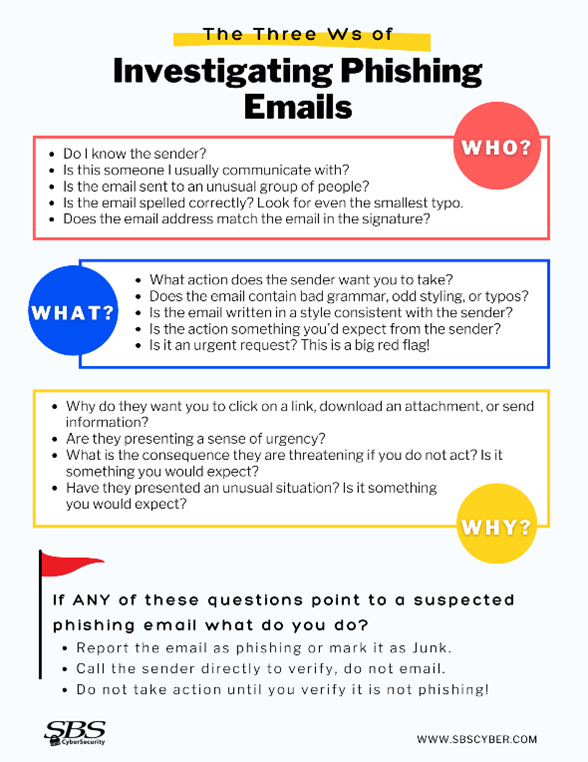
To kick things off, let's talk about one of the most common cyber threats - Phishing Emails. These seemingly innocent emails can be a doorway for hackers to steal your personal and business information. Be cautious of any unexpected emails asking for sensitive information, always double-check the sender's address, and never click on suspicious links! See the infographics below for more red flags.
Remember, your safety is in your hands. Let's work together to create a safer digital environment for everyone!
Stay tuned for more tips and remember to share them with your friends and family because when it comes to cyber security, every click matters!